In any organisation, incident management plays a crucial role in ensuring safety, compliance, and operational efficiency. Whether in healthcare, finance, or local government, a well-structured incident management system is vital for handling risks and incidents effectively. Camms provides a robust solution for managing incidents through its Incident User Roles and Permissions feature, which allows organisations to tailor access and responsibilities based on workflows.
This guide will walk you through the key components of setting up user roles, assigning permissions, and maximising efficiency using the solution.
Why Are User Roles and Permissions Important?
Organisations deal with a variety of incidents, ranging from workplace accidents in manufacturing to data breaches in financial institutions. Without structured access control, incident data can be mismanaged, leading to inefficiencies and compliance risks.
Camms’ User Roles and Permissions system enables organisations to:
- Ensure data security by restricting access based on role-specific needs.
- Improve efficiency by allowing the right users to take action based on their responsibilities.
- Maintain compliance with industry regulations by ensuring that only authorised personnel can modify or view sensitive incident data.
- Establish clear accountability with defined permissions and responsibilities.
By leveraging this feature, businesses can streamline incident reporting and resolution, reducing operational risks and improving organisational response times.
Setting Up Incident User Roles in Camms
Configuring user roles in Camms ensures that each stakeholder has the appropriate level of access within the incident management framework. Here is how you can do it:
Creating a New User Role
- Navigate to Incident Settings from the Mega Menu.
- Select User Role Settings, where all existing user roles are displayed.
- Click the New button to create a fresh user role.
- Enter a Role Name and an optional description.
- Select a Workflow that the role will be associated with (e.g., Near Miss, Office Inspection, etc.).
- Assign permissions based on workflow-specific needs.
- Click Save to finalise the new role.
Example: A hospital might create a role called ‘Near Miss Creator’ for staff responsible for reporting patient safety incidents.
For step-by-step instructions and additional details, refer to the Camms User Guide.
Assigning User Roles to Individuals
Once a user role is created, it must be assigned to a user.
- Navigate to Incident Settings > User Settings.
- Search for the user and open their profile.
- Under User Roles, select the appropriate role from the dropdown.
- Click Save to finalise the assignment.
Example: A finance company might assign the ‘Incident Reviewer’ role to compliance officers who oversee security breaches.
For a step-by-step walkthrough on setting up user roles and permissions in Camms, watch our webinar and gain deeper insights into optimising access control within your organisation.
Understanding Standard Permissions
Permissions in Camms dictate what actions users can take within the system. These are divided into two main categories:
- Standard Permissions: These control access to incident settings, registers, and confidential records.
- Object-Based Permissions: These dictate access levels (view, edit, delete) for specific objects in an incident record.
Key Standard Permissions Include:
- Incident Add Permission: Allows users to create new incidents.
- Display All Records in Registers: Grants visibility over all incidents within a workflow, including both open and closed statuses.
- View Draft Incidents: Enables users to access records still in draft status.
- Hierarchy-Based Permissions: Restrict access according to organisational hierarchy and role-based responsibilities.
Understanding Object-Wise Permissions
In addition to standard permissions, object-wise permissions allow administrators to define user access to specific components within an incident record. This ensures that each user has the right level of control over critical data while maintaining security and compliance.
Key Object-Wise Permissions
| Permission | Description |
|---|
| Edit | Edit Allows users to modify the details of an object. |
| View | Grants read-only access without modification rights. |
| Delete | Enables the removal of records, applicable only to detailed objects. |
| Edit Workflow/Accountability | Permits users to assign incident types and responsible officers. |
| Edit Priority/Severity | Allows users to set or modify an incident’s priority and severity level. |
| Edit Custom Table Record | Provides the ability to update custom table records linked to an object. |
| Delete Custom Table Record | Enables users to remove custom table records, provided they also have ‘Edit’ permissions. |
| Add | Allows users to add the details for an object. |
Best Practices for Applying Object-Wise Permissions
| Scenario | Best Practice |
|---|
| Standard Incident Objects | Users need the ‘Standard Incident Add Permission’ to create incident records. |
| Standard and Custom Objects | The ‘View’ permission must be enabled alongside ‘Edit’ or ‘Delete’ to perform actions. |
| Document Objects | With only ‘View’ permission, users can access and download files but not modify them. |
| Custom Table Records | Require both ‘Edit Custom Table Record’ and ‘Delete Custom Table Record’ permissions for full control over entries. |
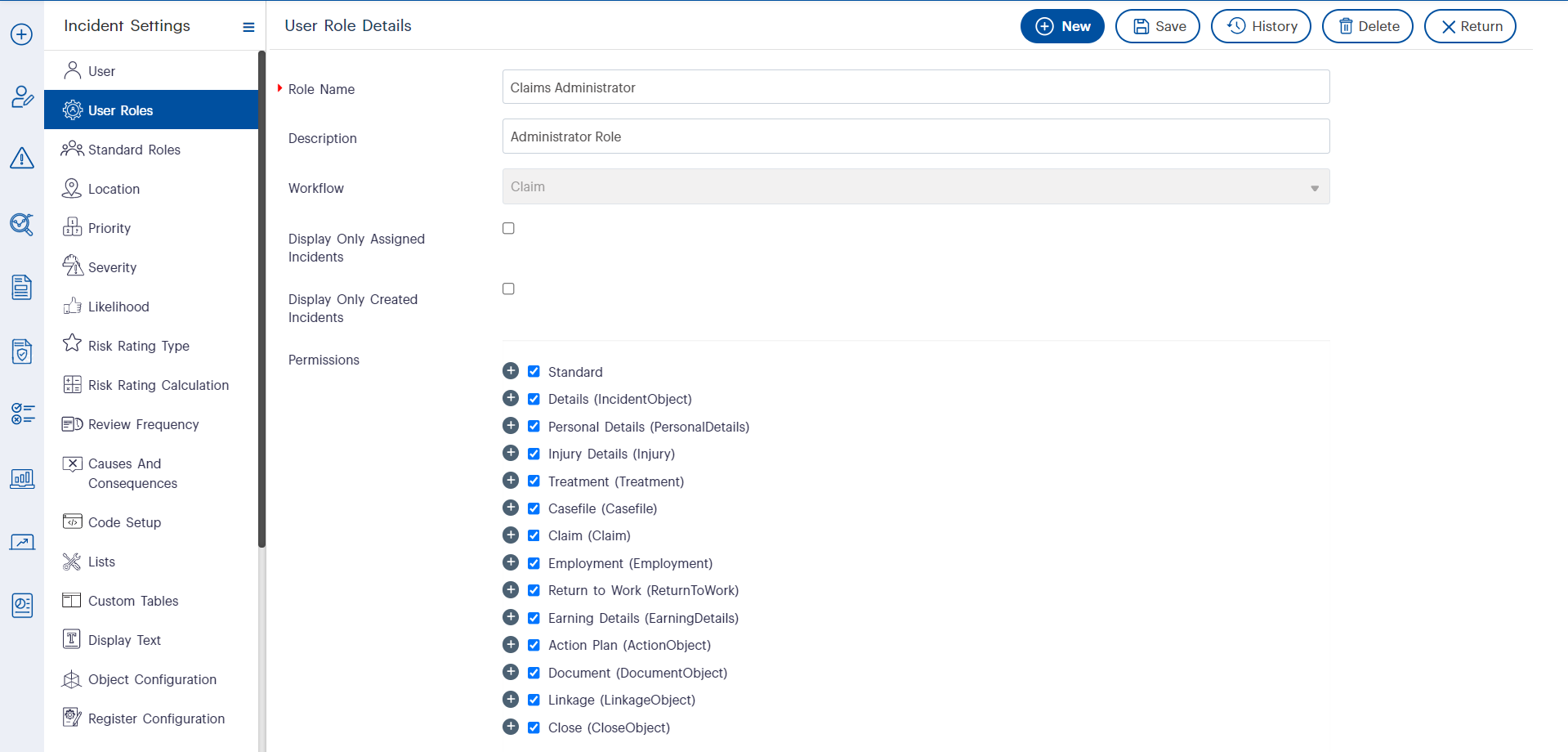 Fig 1.0: User Role Configuration in Incident Settings – Defining Permissions for a Claims Administrator Role
Fig 1.0: User Role Configuration in Incident Settings – Defining Permissions for a Claims Administrator Role
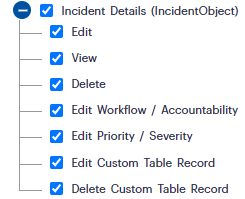 Fig 1.1: Incident Details Permissions – Configuring Access Levels for Editing, Viewing, and Managing Incident Records
Fig 1.1: Incident Details Permissions – Configuring Access Levels for Editing, Viewing, and Managing Incident Records
How Camms Helps Different Industries
Local Government
Challenge: Managing public safety incidents efficiently. Solution: Camms ensures that local government officers have appropriate access to incident reports, allowing for swift resolution of public complaints.
Healthcare
Challenge: Ensuring compliance with patient safety regulations. Solution: Hospitals can assign permissions to specific medical personnel, ensuring only authorised users can handle sensitive incident reports.
Finance
Challenge: Mitigating cyber security threats and fraud incidents. Solution: Camms allows financial institutions to limit access to high-risk data, ensuring compliance with regulatory requirements.
Advanced Role Management: Standard & Custom Roles
Camms also supports Standard Roles that automatically inherit permissions based on predefined responsibilities. These include:
- Incident Responsible Officer: Assigned to those responsible for overseeing incident resolutions.
- Incident Investigator: For personnel tasked with conducting in-depth investigations.
- Incident Sign-Off Authority: For executives who approve or close incidents.
Users can also create Custom Standard Roles for workflow-specific needs. For example, an airline might create a ‘Flight Safety Investigator’ role tailored to aviation-related incidents.
Incident Role Management Permissions in Camms
In addition to user roles and object-wise permissions, Incident Role Management Permissions provide high-level access control across all incident workflows in Camms. These permissions govern user access to incident registers, reports, and hierarchy linkages, ensuring centralised governance over incident data.
Key Features of Incident Role Management Permissions
- Workspace & Menu Access – Controls visibility of the Incident Register, Dashboards, and Analysis Tools.
- Register Visibility Rules – Determines access based on hierarchy assignments, incident responsibility, or ownership.
- Hierarchy-Based Access – Allows users to link incidents only to permitted organisational nodes.
Configuring Incident Role Management Roles
- Go to Role Management in the Strategy module.
- Create a new role and set the product as “Incident”.
- Define access permissions for workspace, registers, and reports.
- Set register visibility rules:
- View All – Access to all open and closed incidents.
- View Node Only and View Node with Children – Limits access to assigned hierarchy nodes.
- View All Created – Shows only user-created incidents.
- View All Responsible Officer – Displays incidents where the user is responsible.
- Assign hierarchy permissions to control which hierarchies users can link incidents to.
Use Case: Secure, Role-Based Access
For example, an IT Security Manager needs access to cyber incidents but not HR cases. By configuring View All Responsible Officer and View Node with Children, they can access only relevant incidents, ensuring security and compliance.
How Camms Supports Your Organisation
Camms helps organisations:
- Reduce manual workload with automated role assignments.
- Enhance incident transparency through structured permissions.
- Strengthen regulatory compliance by controlling access to sensitive information.
- Improve incident response times by ensuring the right people have access to the right data.
To learn more, check out our latest webinar or reach out to our team for a personalised consultation.
Bringing It All Together
By effectively leveraging User Roles and Permissions in Camms, organisations can enhance their incident management processes, ensuring security, efficiency, and compliance. Having the right access controls in place is essential to minimising risks and improving organisational resilience.
Take control of your incident management with Camms. Start configuring your user roles today for a more secure and efficient process.
Become part of the Camms Community and engage in discussions on incident management. Connect with industry experts and fellow users to explore platform features, share insights, and enhance your expertise.












